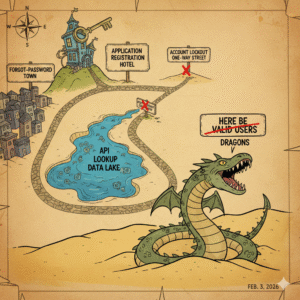
Hey! It’s been awhile since the last AppSec Travels blog. In this post we wanted to write about a vulnerability that is near and dear to our hearts: User Enumeration. In the world of application security, some vulnerabilities are loud and catastrophic, while others are subtle, acting as silent facilitators for more significant attacks. User […]
Redpoint Security Blog
Thoughts on the new OWASP Top Ten
The 2025 OWASP Top 10 is here, and it might be my gray hair speaking, but it seems everything old is new again. For old hats–like myself, who relied on the initial 2003 list to guide my early penetration testing career (thank you, Classic ASP, for the good times)–the 2025 list has less shocking revelations […]
SDLC – Managing risk in Software through the compounding effect of control gates
By Cameron White If you’ve ever watched someone run the hurdles in a track meet, you may share my amazement at their agility to consistently leap each hurdle at speed when the pressure to perform is on. The compounding exertion to clear each barrier is not hard to imagine, and when you’re trying it yourself, […]
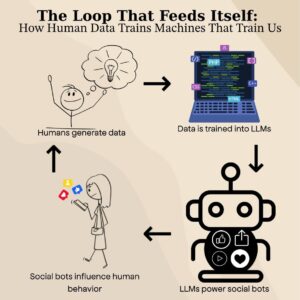
The Loop that Feeds Itself: How human data trains machines that train us
A decadent introduction by Jade Lee Our world is made up of an astronomical amount of data. Beyond internet traffic and hard drives, we now supply a consistent stream of data through our cars, refrigerators, doorbells, and most importantly, our words. Almost the entire expanse of human thought and home can be translated into vector embeddings, […]
Navigating the AI Frontier: How Redpoint Security is Integrating Artificial Intelligence into Application Security
Artificial intelligence is rapidly transforming industries, and application security is no exception. At Redpoint Security, we’ve been on a journey to understand and leverage the power of AI, not just to enhance our own capabilities, but also to help our clients navigate the evolving threat landscape and securely incorporate AI into their own applications and […]
Breaking Bad: How to Identify and Overcome Destructive Fatigue
Introduction In fields that require constant analysis, critique, and problem-solving—such as information security, auditing, and quality assurance—there’s a unique form of burnout that many professionals experience: destructive fatigue. Unlike traditional burnout, which is often tied to excessive workload, destructive fatigue stems from the mental toll of constantly tearing things down without opportunities to build. This […]
How AI and LLMs Will Shape AppSec in 2025
Four Predictions for AppSec in 2025 By Ken Johnson and Seth Law In this joint blog from Seth Law at Redpoint and Ken Johnson at DryRun Security, we highlight how 2025 will be a pivotal year for large language models (LLMs) in AppSec. Building on the momentum of 2024, LLMs are moving from novelty to […]
Redpoint Security Interns at DEFCON32
Adelyn Wengreen, a first-time Def Con attendee My first experience at DEF CON was awesome. As someone still new to this industry, I had no idea what to expect going in, but I really enjoyed the whole weekend. My favorite presentation was My Conversations With a GenAI-Powered Virtual Kidnapper by Perry Carpenter. He talked about […]