Four Predictions for AppSec in 2025 By Ken Johnson and Seth Law In this joint blog from Seth Law at Redpoint and Ken Johnson at DryRun Security, we highlight how 2025 will be a pivotal year for large language models (LLMs) in AppSec. Building on the momentum of 2024, LLMs are moving from novelty to […]
Services
The experience of a beginner in the field of Appsec.
My name is Trevon Greenwood, and I am a Junior Security Analyst at Redpoint Security. This post outlines my experience as a beginner in the field and what a day at work looks like for me. I have been with Redpoint for just over a year now, so I think I’ve accrued enough experience as […]
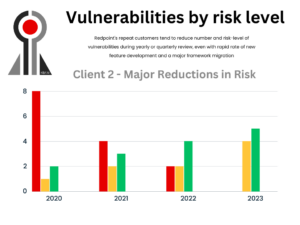
A Redpoint Customer Security Journey
In Redpoint Security’s existence as an application security firm, we have seen a range of clientele who manifest a whole host of differences: development teams and applications that range remarkably small and large, different levels of security maturity, compliance requirements that are relatively lax as opposed to highly demanding with a rapidly rushing SLA (Service-Level […]
AppSec Travels Part 2: Access-Control Bypass
What happens when combined technologies counteract security controls? This is another in Redpoint’s blog series AppSec Travels where we walk you through interesting findings we’ve discovered in vulnerability assessments. AppSec Travels is on ongoing series without a regular cadence because frankly some assessments are perfunctory security checks lacking in exciting findings and we sort of […]
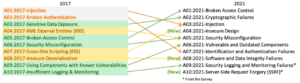
Training Devs for a new OWASP Top Ten
What we learned from adapting our Application Security 101 course Background: The OWASP Top Ten – An Awareness Document The OWASP Top Ten is a widely-used guide developed by the fine folks at the Open Web Application Security Project that provides a list of the common and critical vulnerabilities in web applications. First published in […]
Redpoint Services
Application Security in 2024: A Look at Redpoint’s Service Offerings In today’s rapidly changing landscape of information security, protecting your applications is crucial. The statistics speak for themselves: data breaches can incur significant costs, with an average cost of $4 million per breach, according to IBM. It’s clear that the threat of exploitation is widely […]