Four Predictions for AppSec in 2025 By Ken Johnson and Seth Law In this joint blog from Seth Law at Redpoint and Ken Johnson at DryRun Security, we highlight how 2025 will be a pivotal year for large language models (LLMs) in AppSec. Building on the momentum of 2024, LLMs are moving from novelty to […]
Code Security
AppSec Travels 3: Account Takeover
During a recent assessment, our team came upon a vulnerability that felt like finding a hidden door in a seemingly secure fortress. The discovery involved the password-reset mechanism of an application, allowing us to reset any user’s password with just their email address. This flaw circumvents authentication, giving unauthorized access to user accounts. Here’s how […]
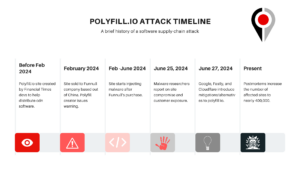
Polyfill io and Surveyor’s Continuous Dependency Monitor
In the aftermath of the polyfill supply-chain attack that reportedly compromised the security of some 100,000 applications across the Internet last week (arstechnica reports that over 384K sites are still pulling the package subsequently), our team at Redpoint realized quickly that it was a real-world case of feature within Redpoint’s Surveyor tool. That is, lead […]
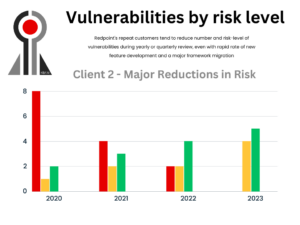
A Redpoint Customer Security Journey
In Redpoint Security’s existence as an application security firm, we have seen a range of clientele who manifest a whole host of differences: development teams and applications that range remarkably small and large, different levels of security maturity, compliance requirements that are relatively lax as opposed to highly demanding with a rapidly rushing SLA (Service-Level […]
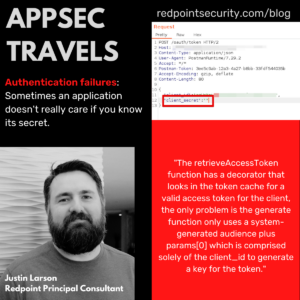
AppSec Travels Part I: Function Overload
Token Caching This is our first blog of AppSec Travels where we walk you through interesting findings we’ve discovered in vulnerability assessments. This will be on ongoing series without a regular cadence because frankly some assessments are perfunctory security checks lacking in exciting findings and we sort of doubt anyone wants to read findings write-ups […]
Redpoint Services
Application Security in 2024: A Look at Redpoint’s Service Offerings In today’s rapidly changing landscape of information security, protecting your applications is crucial. The statistics speak for themselves: data breaches can incur significant costs, with an average cost of $4 million per breach, according to IBM. It’s clear that the threat of exploitation is widely […]
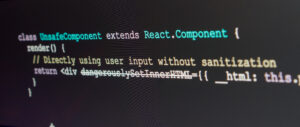
Redpoint and Code
Why code security by coders? The secret to comprehensive security is knowing how an attacker thinks and how a developer creates. The important thing to remember for finding and helping remedy security flaws, is that it requires assessments where our testers/researchers can toggle between two frames of mind. First, We look at your application like […]