My name is Trevon Greenwood, and I am a Junior Security Analyst at Redpoint Security. This post outlines my experience as a beginner in the field and what a day at work looks like for me. I have been with Redpoint for just over a year now, so I think I’ve accrued enough experience as […]
Redpoint Assessment Process
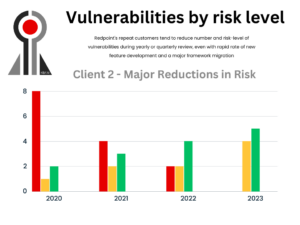
A Redpoint Customer Security Journey
In Redpoint Security’s existence as an application security firm, we have seen a range of clientele who manifest a whole host of differences: development teams and applications that range remarkably small and large, different levels of security maturity, compliance requirements that are relatively lax as opposed to highly demanding with a rapidly rushing SLA (Service-Level […]
Redpoint Services
Application Security in 2024: A Look at Redpoint’s Service Offerings In today’s rapidly changing landscape of information security, protecting your applications is crucial. The statistics speak for themselves: data breaches can incur significant costs, with an average cost of $4 million per breach, according to IBM. It’s clear that the threat of exploitation is widely […]
Redpoint and Code
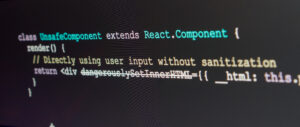
Why code security by coders? The secret to comprehensive security is knowing how an attacker thinks and how a developer creates. The important thing to remember for finding and helping remedy security flaws, is that it requires assessments where our testers/researchers can toggle between two frames of mind. First, We look at your application like […]