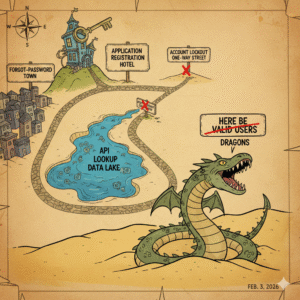
Hey! It’s been awhile since the last AppSec Travels blog. In this post we wanted to write about a vulnerability that is near and dear to our hearts: User Enumeration. In the world of application security, some vulnerabilities are loud and catastrophic, while others are subtle, acting as silent facilitators for more significant attacks. User […]
Findings Writeup
AppSec Travels 3: Account Takeover
During a recent assessment, our team came upon a vulnerability that felt like finding a hidden door in a seemingly secure fortress. The discovery involved the password-reset mechanism of an application, allowing us to reset any user’s password with just their email address. This flaw circumvents authentication, giving unauthorized access to user accounts. Here’s how […]
AppSec Travels Part 2: Access-Control Bypass
What happens when combined technologies counteract security controls? This is another in Redpoint’s blog series AppSec Travels where we walk you through interesting findings we’ve discovered in vulnerability assessments. AppSec Travels is on ongoing series without a regular cadence because frankly some assessments are perfunctory security checks lacking in exciting findings and we sort of […]
AppSec Travels Part I: Function Overload
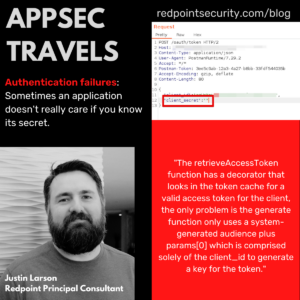
Token Caching This is our first blog of AppSec Travels where we walk you through interesting findings we’ve discovered in vulnerability assessments. This will be on ongoing series without a regular cadence because frankly some assessments are perfunctory security checks lacking in exciting findings and we sort of doubt anyone wants to read findings write-ups […]