In the aftermath of the polyfill supply-chain attack that reportedly compromised the security of some 100,000 applications across the Internet last week (arstechnica reports that over 384K sites are still pulling the package subsequently), our team at Redpoint realized quickly that it was a real-world case of feature within Redpoint’s Surveyor tool. That is, lead developers @Seth and @Justin have implemented a continuous monitor of client-observed, critical packages and software dependencies. It has been no small undertaking, but we recognized the value in being able to establish a baseline of scripts and packages in use by an application and to survey those packages for changes that suggest increased risk.
Surveyor as an security application is really comprised of three unique tools:
- A client-side code monitoring tool
- A dynamic application scanner that provides Continuous Attack Surface Monitoring
- A continuous dependency monitor
The client-side code monitor was the first tool developed by the Redpoint Labs Surveyor development team. It works to survey in-use application code and scripts every time the application is served to a customer. In this case, any Magecart (or Polyfill) style attack that serves suspicious malware or JavaScript card-skimming injections are immediately recognized by Surveyor.
Redpoint initially produced this monitor to be alerted when new and unexpected scripts were loaded on sensitive customer sites, which subsequently solved the typical 200-day lag between a client-side injection attack and an organization’s discovery of that attack. Surveyor alerts immediately by watching what customers see, rather than relying on happenstance reports from a server-side monitor or, even worse, a customer report of a malicious user loading mysterious charges on their credit card after they’d used your site.
Redpoint developers quickly learned that there were more applications to the client-side monitoring tool. A dynamic application scanner works astonishingly well as a continuous attack surface monitor for your application because client-side context and detection triggers alerts when assets move or when your application changes behavior.
This client-side detection also works wonders for noticing when your application’s dependencies begin shifting locations and swap out trusted maintainers for unknown ones.
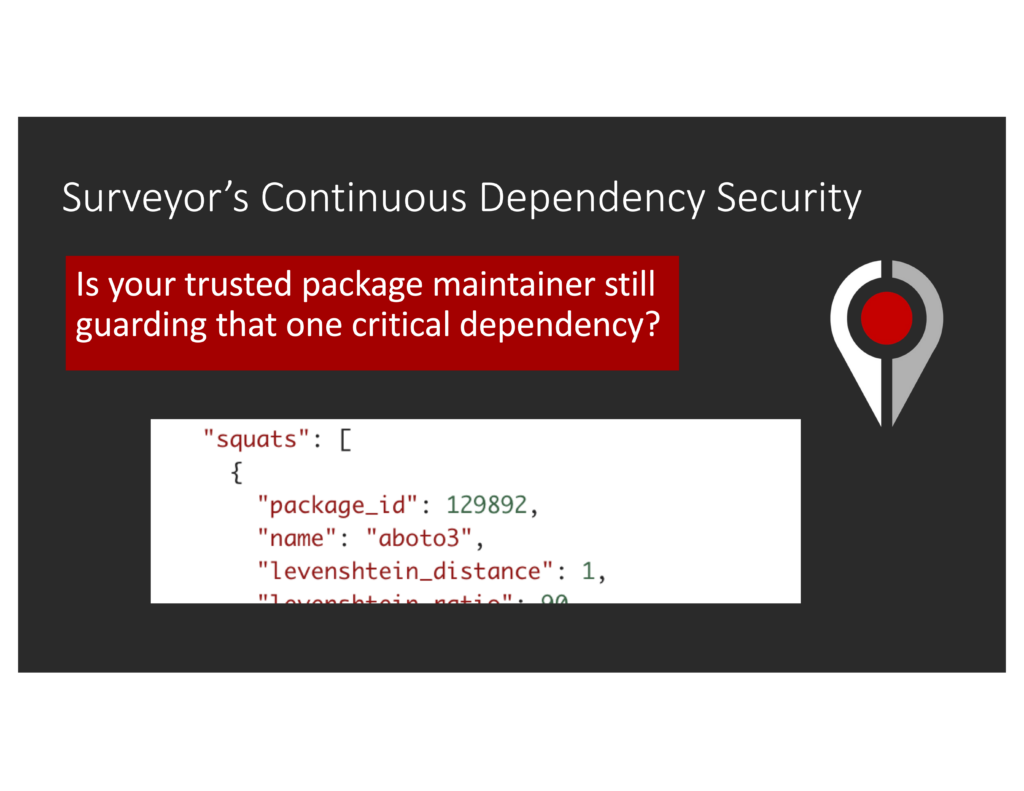
How Surveyor would alert for the polyfill attack
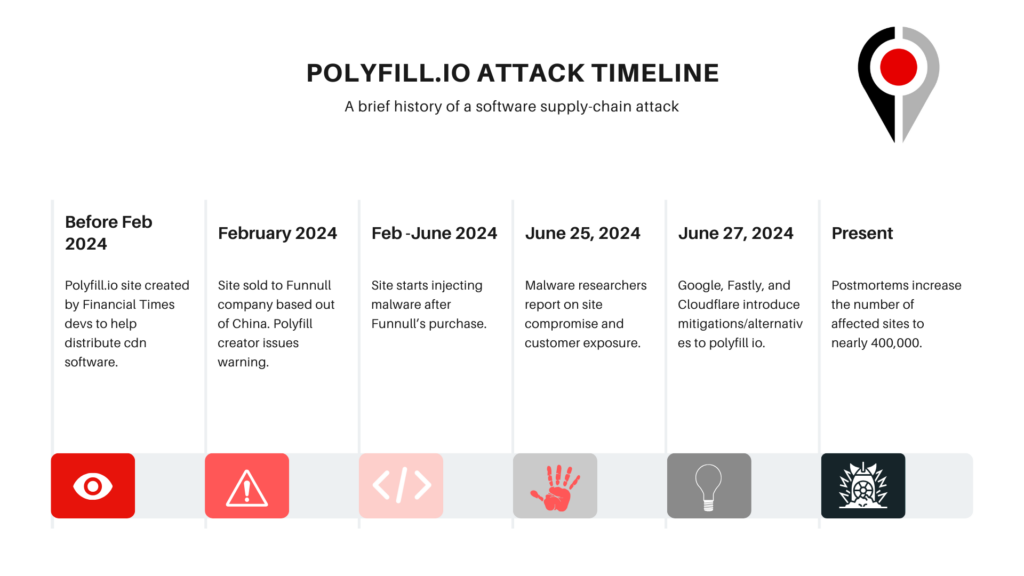
Surveyor keys off a number of different indicators for analysis. Any change in script source code results in immediate notification, as would metadata changes to a package maintainer or hosting provider. On its surface, Surveyor can be considered a background check for dependencies, where script source, package details, and its maintainer are taken into account to gauge threat. The sale of a domain to another country would result in an alert generated regarding the change to a monitored dependency. As news of the hack and exposure began to trickle in, we noted that the several-month lag between that risky ownership change, the compromise of the package, and the discovery of the malicious software that began being distributed to polyfill io users, was entirely too long.
If you have interest in finding out more about Surveyor, reach out to us here at Redpoint Security. Continuous Dependency Monitoring is just one arrow in Surveyor’s quiver helping our customers secure their applications. We’ll meet with you to demonstrate how Surveyor works and show you how it can solve some of the trickier problems presented by modern applications. Reach out to us today to see how we can help.