Redpoint Security principals and developers have worked on a proprietary tool, Surveyor, which provides full visibility into an application’s security posture by monitoring common weak spots and using your application customers to trigger reporting.
Secure your web application from Build to Browser
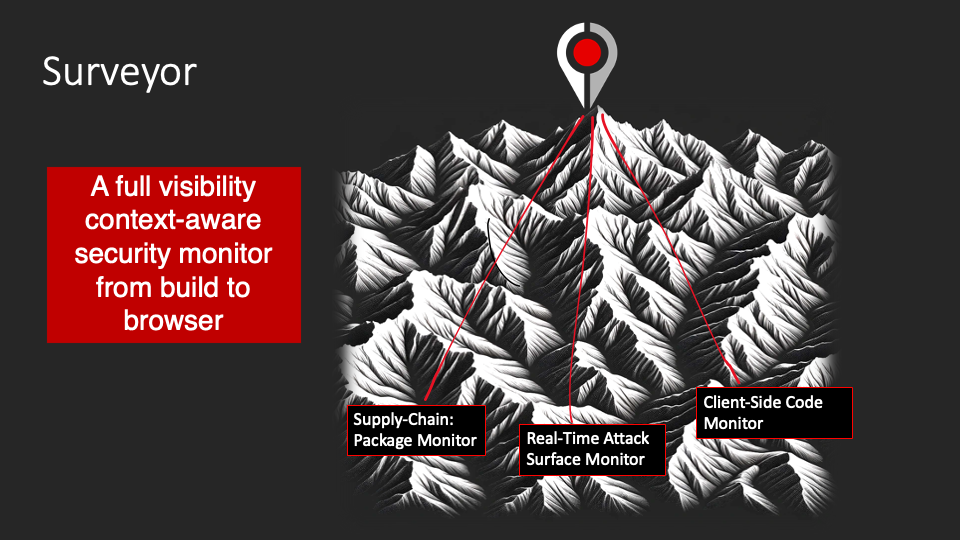
Surveyor works to secure your application by providing a real-time monitor for three key stages in your application’s lifecycle. That’s why we argue that Surveyor is security from build to browser. Surveyor provides coverage for teams concerned about your SDLC, your application’s runtime security, as well as sneaky attacks against your customers and their data that often don’t get discovered. Surveyor provides this security in three key ways.
- Activating a Package Monitor that alerts you to changes to packages for keystone components and libraries that your application depends on.
- By monitoring runtime application behavior. Surveyor, in the initial review of the application, creates a baseline for the application’s operations and interactions, and it reports anytime it sees a change to that baseline.
- By monitoring the application your customer sees in the browser, Surveyor can tell you if a malicious JavaScript is operating on the customer’s page, providing instant notification that credit-card skimming or magecart-style attacks may be taking place against your customers.
Redpoint testers already use Surveyor in application review because, as a browser plugin, it works to start mapping out an application’s attack surface as well as alerting on potential vulnerabilities that may exist in initial reviews. If you’d like to learn more about Surveyor, check out the Redpoint Labs site, or contact Redpoint below for more information.
General FAQs
- Application and User Behavior Monitor - this is the feature that could be described as Google Analytics for Security Events. That means analyzing User Behavior, Application Behavior and JavaScript Analysis that detects and reports potentially risky behaviors and changes of interest over time.
- Continuous Dynamic Assessment - this feature is implemented in Redpoint Security's application security assessment process already. Surveyor performs scans of an application, so we can provide host reports that combine asset discovery and attack surface monitoring that alerts on common vulnerabilities we find during our application reviews. From this data, Surveyor and Redpoint Security testers provide custom developed Security Unit Tests from data gathered during Surveyor scans and our expert-driven application assessments.
- Supply-Chain Package Monitor - With this feature, Surveyor will alert you if there are changes to critical dependencies, and those alerts will include threat assessment of whether those changes raise risk of a supply-chain attack. The information you get from a Supply-Chain alert goes further than a typical SCA or SBOM report because it digs into Package metadata, so you'll know if your most critical package has changed ownership (as was the case with the polyfill io attack) or even if the package has a new maintainer. Surveyor's run-time triggers means that something like the polyfill io attack would have been registered and alerted on within minutes, rather than the 6 months it did take
- an Application and User Behavior Monitor, this is the feature that could be described as Google Analytics for Security Events. That means analyzing User Behavior, Application Behavior and JavaScript Analysis that detects and reports potentially risky behaviors and changes of interest over time.
- Continuous Dynamic Assessment, this feature is implemented in Redpoint Security's application security assessment process already. Surveyor performs scans of an application, so we can provide host reports that combine asset discovery and attack surface monitoring that alerts on common vulnerabilities we find during our application reviews. From this data, Surveyor and Redpoint Security testers provide custom developed Security Unit Tests from data gathered during Surveyor scans and our expert-driven application assessments.
- Supply-Chain Package Monitor - With this feature, Surveyor will alert you if there are changes to critical dependencies, and those alerts will include threat assessment of whether those changes raise risk of a supply-chain attack. The information you get from a Supply-Chain alert goes further than a typical SCA or SBOM report because it digs into Package metadata, so you'll know if your most critical package has changed ownership (as was the case with the polyfill io attack) or even if the package has a new maintainer. Surveyor's run-time triggers means that something like the polyfill io attack would have been registered and alerted on within minutes, rather than the 6 months it did take.
- Simple Signup and Setup: It's as quick as setting up an account, taking the script Surveyor provides you, and placing it on the application host you'd like to have watched. You can even try it on single host today to see how it works.
- Speed of Notifications: Alerts for changes to application scripts, package monitors, or your application's attack surface are triggered when a customer loads a page with those changes on it. The speed of our solution works quite differently from a server-side scanner that may not register a change for weeks at a time. We use the polyfill io example when we talk about this difference because it's true, Surveyor would have told you about the polyfill io compromise the second the package was acquired by a new potentially malicious maintainer. It would have also told you that there were indicators that the new maintainer had an elevated risk profile, before malicious scripts were even loaded into the package.
- Reliability of Findings: Surveyor has been trained on Redpoint Security's own processes that aim to provide findings that are accurate, useful, and whenever possible, actionable with remediation recommendations. Furthermore, with Surveyor we make use of Machine-Learning tools to continuously improve its output. That means continuous awareness of emerging threats, and more accurate rankings over time. Overall, you'll be able to trust that findings Surveyor notifies you about, and the risk ratings you receive have a weight behind them.